
 |
All About Firewalls |
|
|
PIX firewallThe PIX is a firewall appliance based on a hardened, specially built operating system, PIX OS, minimizing possible OS-specific security holes. The PIX has received ICSA Firewall and IPsec certification as well as Common Criteria EAL4 evaluation status. PIX firewalls provide a wide range of security and networking services including: 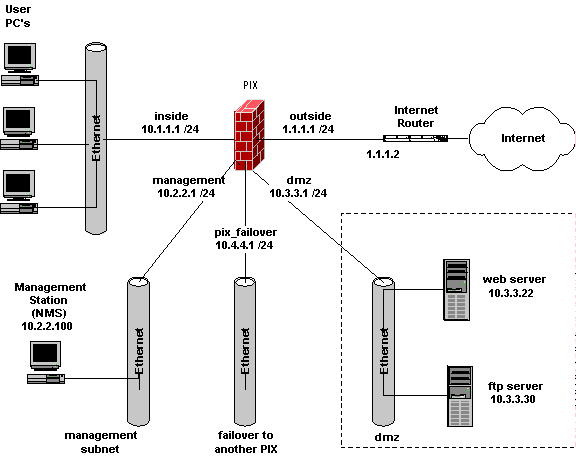 PIX terminology: we generally refer to the user segment as the Inside subnet. The interface connected to the Internet router is the outside subnet. As shown, we probably have DMZ (De-Militarized Zone) subnet, the subnet where we quarantine all servers that are accessible from the outside. We might also have a separate management subnet and a subnet tying to a redundant PIX for failover (if supported/licensed). The PIX Command-Line Interface (CLI) is somewhat like the Cisco IOS interface, but different. Use colon (":") for comments (which, as usual, are not retained). Newer PIX OS uses ACL's, replacing the former conduits (which were arguably more confusing to experienced Cisco router administrators). PIX interfaces are normally shutdown until the administrator activates them. PIX interfaces have an associated security level. Two interfaces at same level can't send packets to each other. We'll shortly see that you set levels with nameif command. Connections and traffic are normally permitted from higher to lower security level interfaces, although you do have to put in some basic configuration to allow traffic to flow. Connections the other way (from low to high security) are disallowed unless the configuration explicitly permits them. |