
 |
All About Firewalls |
|
|
Application-level GatewayLike a circuit-level gateway, an application-level gateway intercepts incoming and outgoing packets, runs proxies that copy and forward information across the gateway, and functions as a proxy server, preventing any direct connection between a trusted server or client and an untrusted host. However, the proxies that an application-level gateway runs differ in two important ways from the pipe proxies that a circuit-level gateway uses: The proxies are application specific. 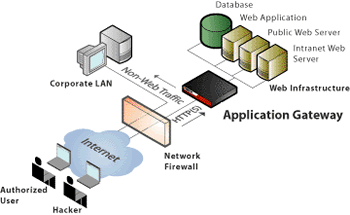 Application-specific Proxies. Unlike pipe proxies, application-specific proxies accept only packets generated by services they are designed to copy, forward, and filter. For example, only a Telnet proxy can copy, forward, and filter Telnet traffic. If a network relies only on an application-level gateway, incoming and outgoing packets cannot access services for which there is not a proxy. For example, if an application-level gateway ran FTP and Telnet proxies, only packets generated by these services could pass through the firewall. All other services would be blocked. Application-level Filtering. Unlike a circuit-level gateway, an application-level gateway runs proxies that examine and filter individual packets, rather than simply copying them and blindly forwarding them across the gateway. Application-specific proxies check each packet that passes through the gateway, verifying the contents of the packet up through the application layer (which is the highest layer) of the OSI model. These proxies can filter particular kinds of commands or information in the application protocols the proxies are designed to copy, forward, and filter. Application gateways can also restrict specific actions from being performed. For example, the gateway could be configured to prevent users from performing the FTP put command. This command lets users write to the FTP server. Prohibiting this action can prevent serious damage of the information stored on the server. Transparency--Ah, There's the Rub! An application-level gateway is one of the most secure firewalls available, but some vendors (usually those that market stateful inspection firewalls) and users claim that the security an application-level gateway offers has a drawback--lack of transparency. Ideally, an application-level gateway would be as transparent as it is secure. Users on the trusted network would not notice that they were accessing Internet services through a firewall. In reality, however, users often experience delays or must perform multiple logins before they are connected to the Internet or an intranet via an application-level gateway. Although most vendors claim that application-level gateways are transparent, many vendors recommend that you configure the gateway to require user authentication before users access an untrusted network, a process that foils true transparency. Some firewall vendors that market products as application-level gateways have tried to overcome the transparency problem. For example, one particular application gateway uses a version of the SOCKS protocol (rather than application-specific proxies) to route TCP/IP services. SOCKS is a proposed Internet Engineering Task Force (IETF) standard that provides transparent authentication services for clients requesting connections to devices through firewalls. However, a SOCKS server is not transparent to network administrators: You must modify the applications running on each client that will use the firewall. Also, although SOCKS includes other security features (such as private-key and public-key encryption), it does not filter individual packets. Therefore, the products that rely on SOCKS might fall justifiably into the realm of circuit-level gateways rather than application-level gateways. |