
 |
All About Firewalls |
|
|
Circuit-level GatewayA circuit-level gateway monitors TCP handshaking between packets from trusted clients or servers to untrusted hosts and vice versa to determine whether a requested session is legitimate. To filter packets in this way, a circuit-level gateway relies on data contained in the packet headers for the Internet's TCP session-layer protocol. Because a circuit-level gateway filters packets at the session layer of the OSI model, this gateway operates two layers higher than a packet-filtering firewall does. 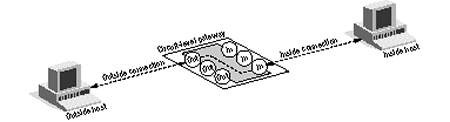 Monitoring Handshaking--Circuitously. To determine whether a requested session is legitimate, a circuit-level gateway uses a process similar to the following: A trusted client requests a service, and the gateway accepts this request, assuming that the client meets basic filtering criteria (such as whether DNS can locate the client's IP address and associated name). Next, acting on behalf of the client, the gateway opens a connection to the requested untrusted host and then closely monitors the TCP handshaking that follows. This handshaking involves an exchange of TCP packets that are flagged SYN (synchronize) or ACK (acknowledge). These packet types are legitimate only at certain points during the session. See the SYNDefender white paper for a more detailed description of the SYN/ACK process. A circuit-level gateway determines that a requested session is legitimate only if the SYN flags, ACK flags, and sequence numbers involved in the TCP handshaking between the trusted client and the untrusted host are logical. Pipe Proxies. After a circuit-level gateway determines that the trusted client and the untrusted host are authorized to participate in a TCP session and verifies the legitimacy of this session, the gateway establishes a connection. From this point on, the circuit-level gateway simply copies and forwards packets back and forth without further filtering them. The gateway maintains a table of established connections, allowing data to pass when session information matches an entry in the table. When the session is completed, the gateway removes the associated entry in the table and closes the circuit this session used. A circuit-level gateway relies on special applications to perform copy and forward services. These applications are sometimes called pipe (or generic) proxies because they establish a virtual circuit, or pipe, between two networks and then allow packets (generated by one or more types of TCP/IP applications) to pass through this pipe. Seldom Standalone. Because pipe proxies generally support several TCP/IP services, a circuit-level gateway can extend the number of services supported by an application-level gateway, which relies on application-specific proxies. In fact, most circuit-level gateways are not stand-alone products but instead are packaged with application-level gateways. Proxy Server Protection. A circuit-level gateway provides one other important security function: It is a proxy server. Although the term proxy server suggests a server that runs proxies (which is true of a circuit-level gateway), the term actually means something different. A proxy server is a firewall that uses a process called address translation to map all of your internal IP addresses to one "safe" IP address. This address is associated with the firewall from which all outgoing packets originate. As a result, on a network with a circuit-level gateway, all outgoing packets appear to have originated from that gateway, preventing direct contact between the trusted network and the untrusted network. That is, a circuit-level gateway's IP address is the only active IP address and the only IP address that the untrusted network is aware of. Thus, a circuit-level gateway and other proxy servers protect trusted networks from spoofing attacks. Circumventing Circuits. A circuit-level gateway does have one inherently vulnerable characteristic, however: Once a circuit-level gateway establishes a connection, any application can run across that connection because a circuit-level gateway filters packets only at the session layer of the OSI model. In other words, a circuit-level gateway cannot examine the application-level content of the packets it relays between a trusted network and an untrusted network. Because a circuit-level gateway does not filter individual packets but blindly relays packets back and forth across established connections, a hacker on an untrusted network could possibly slip malicious packets past the gateway. The hacker could then deal directly with an internal server, such as a WWW server, which may not be as carefully monitored or configured as the firewall itself. As long as the initial TCP packets exchanged between the trusted WWW server and the untrusted host met the handshaking criteria, the gateway would establish a connection and copy and forward subsequent packets--regardless of their content. To filter the application-level content of individual packets generated by particular services, you need an application-level gateway. |